Day - 2 A Comprehensive Guide to AWS Identity and Access Management (IAM)
IAM: Empowering Access Control
AWS IAM is a robust security service that provides fine-grained access control to AWS resources. Its primary objective is to manage user identities, define their permissions, and enforce secure authentication and authorization mechanisms.
Key Components of AWS IAM
- Users: IAM users are the fundamental building blocks of the IAM system. They represent individuals, applications, or services that interact with AWS resources. Each IAM user has a unique name and associated security credentials, such as passwords or access keys, for authentication and access control.
Explanation: Think of IAM users as individual accounts or identities within the IAM system. They are like real people or applications that need access to your AWS resources. Each IAM user has a unique name and specific security credentials (like a username and password or access keys) to securely interact with AWS resources.
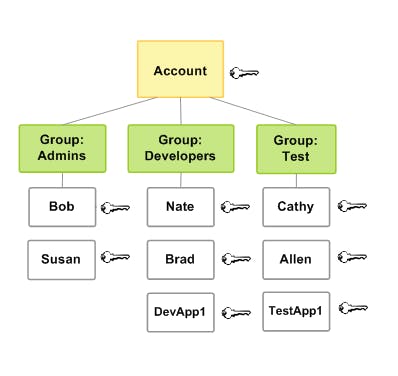
- Groups: To simplify access management, IAM groups allow you to organize users with similar roles and permissions. Instead of configuring permissions for each user individually, you can assign them to groups, reducing administrative overhead and ensuring consistent access control.
Explanation: Imagine IAM groups as collections of users with similar roles or access needs. Instead of setting permissions for each user separately, you can group users together based on their responsibilities. By doing so, you can grant permissions to the entire group at once, simplifying access control and management.
- Roles: IAM roles are a versatile component that grants temporary access to AWS resources. Typically used by applications or services acting on behalf of users or other services, roles have associated policies defining the allowed permissions and actions. This dynamic approach enhances security and minimizes the need for long-term access keys.
Explanation: IAM roles are like temporary credentials used by entities outside of your AWS account. They are often used by applications or services that need to access your AWS resources securely. Roles have associated policies that specify the exact permissions they require. By using roles, you can grant access without sharing long-term access keys, improving security.
Policies: IAM policies, written in JSON format, are the cornerstone of access control within the IAM system. These policies specify the actions that users, groups, or roles can perform on AWS resources and the resources to which these actions apply. By attaching policies to IAM entities, you can effectively control access and enforce the principle of least privilege
.
Explanation: IAM policies are like sets of rules that define what actions are allowed or denied on AWS resources. These policies are written in JSON format and can be attached to users, groups, or roles. By creating policies, you define who can do what in your AWS environment. This allows you to enforce the principle of least privilege, ensuring that each IAM entity has only the necessary permissions needed for their tasks.
Implementing IAM Best Practices
To optimize your IAM configuration and enhance security, follow these best practices:
Principle of Least Privilege: Adhere to the principle of least privilege, granting each IAM entity only the necessary permissions required for their tasks. This minimizes security risks and unauthorized access.
Regular Auditing: Regularly audit IAM entities and permissions to identify any inconsistencies or unnecessary privileges. Remove any unused or outdated permissions to maintain a clean and secure IAM environment.
Multi-Factor Authentication (MFA): Enforce MFA for IAM users to add an extra layer of protection against unauthorized access. MFA requires users to provide an additional authentication factor, making it significantly more challenging for malicious actors to compromise accounts.
Time-Based Access: Leverage IAM roles with time-based permissions to grant temporary access when needed and automatically revoke access when the predefined time window expires.
Conclusion
AWS IAM is a critical component of your cloud security strategy, allowing you to control access to your AWS resources and protect your data. By configuring IAM users, groups, roles, and policies effectively, you can ensure that your cloud environment remains secure, compliant, and resilient to potential threats.